For Chrome users, it is already enabled and you can't disable it because Google.
cd /path/to/widevine # Go to our directory
wget "<the URL you copied>"
Google Widevine is the most widely used DRM (Digital Right Management) technology right now. It is used among the biggest platforms, like Netflix. What does DRM do? It restricts you from copying (downloading locally) the content that you are watching. But I don't like that! So let's break it!
Google divides Widevine's operation security in three levels:
The Content Decryption Module (CDM) does the licensing and decryption of the content. To get one, we need to dump it from an Android phone. To do this, we will start an Android emulator and dump the Widevine CDM from it. I you already have installed Android Studio, you can create an AVD (API 28) using the GUI tools. If you don't, I will show you how to do it without using Android Studio.
I am using Linux to do this. If you are using Windows, please download Android Studio and set up an AVD from there. Steps:
cd ~
mkdir -p Android/Sdk
cmdline-tools/
└── latest
├── bin
├── lib
├── NOTICE.txt
└── source.properties
cd Android/Sdk/cmdline-tools/latest/bin
./sdkmanager --licenses
./sdkmanager "emulator" "platform-tools" "platforms;android-28" "system-images;android-28;google_apis;x86_64"
./avdmanager create avd -n "wvdump" -k "system-images;android-28;google_apis;x86_64"
Now we need to install something called the "Frida Server" to our emulator, so that the program that dumps the CDM can communicate with the emulator. Steps:
pip3 install frida
pip3 install frida-tools
cd ~/Android/Sdk/emulator
./emulator -avd wvdump
And then wait for the emulator to start. If you have a slow computer, this will take a while.
cd ~/Android/Sdk/platform-tools
./adb push /path/to/frida-server-X.X.X-android-x86_64 /sdcard
./adb shell
mv /sdcard/frida-server.X.X.X-android-x86_64 /data/local/tmp
chmod +x /data/local/tmp/frida-server.X.X.X-android-x86_64
/data/local/tmp/frida-server.X.X.X-android-x86_64
You will see that it will wait indefinitely. This is good and it means that the Frida Server is running.Now we will finally dump the CDM from the device.
mkdir widevine && cd widevine
git clone https://github.com/wvdumper/dumper.git
cd dumper
pip3 install -r requirements.txt
pip3 install protobuf==3.20.0 # We downgrade the library version to avoid a weird crash
python3 dump_keys.py
You will see that it will wait for activity.
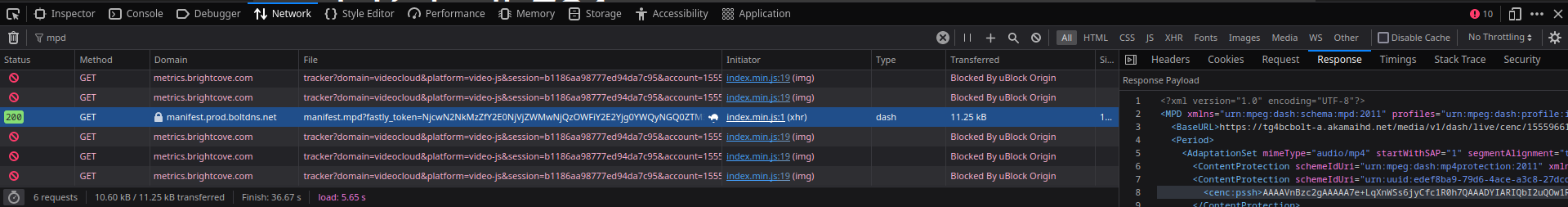
Now we should choose a video to decrypt. The site tg4.ie
is a pretty good site for you to practice, because it provides video encrypted with Widevine and a relatively easy procedure to follow.
To get the keys required for the decryption we need three things:

cd /path/to/widevine # Go to our directory
wget "<the URL you copied>"
We will do this with the help of a library/tool named pywidevine. Steps:
pip3 install pywidevine
pywidevine create-device -t ANDROID -l3 -k /path/to/private_key.pem -c /path/to/client_id.bin -o device.wvd
Replace the paths to your CDM files appropriately.
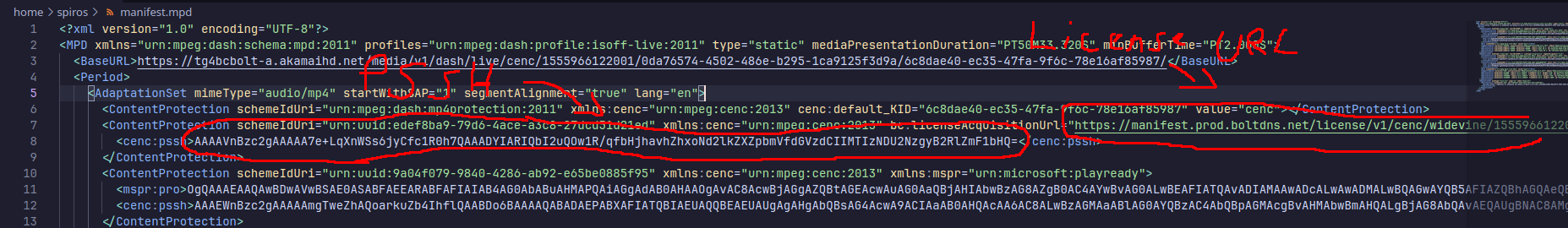
pywidevine license device.wvd <PSSH> <License URL>
Replace the PSSH and License URL appropriately.
The output should be similiar to this:
INFO:root:pywidevine version 1.8.0 Copyright (c) 2022-2024 rlaphoenix
INFO:root:https://github.com/devine-dl/pywidevine
INFO:license:[+] Loaded Device (4464 L3)
INFO:license:[+] Loaded CDM
INFO:license:[+] Opened CDM Session: 9a5a570efca927a4db506d40e5deb27b
INFO:license:[+] Created License Request Message (Challenge)
INFO:license:[+] Got License Message
INFO:license:[+] License Parsed Successfully
INFO:license:[SIGNING] 00000000000000000000000000000000:56398c5cb0287ba52085be71c2aeb5b0d61d9b6cd6eec441c442c455832862cbad123c97fed82139156a755c79c4331843379140ca9ea0c37547e693e4827092
INFO:license:[CONTENT] 6c8dae40ec3547fa9f6c78e16af85987:f05de262d9b1b3db398d153edf0bf80b
The pair of big hexadecimal numbers after [CONTENT] is our key (and key ID)! Copy it and save it to a file.
Finally, to decrypt the audio and video (as you may have noticed there two separate files) we will need a copy of the Bento4 SDK. Download it and extract it. To decrypt do:
/path/to/Bento4-SDK/bin/mp4decrypt --key <The key we got earlier> video.mp4 video_decrypted.mp4
/path/to/Bento4-SDK/bin/mp4decrypt --key <The key we got earlier> audio.m4a audio_decrypted.m4a
Replace the key with the full key and key id pair we got before (with the : , e.g 6c8dae40ec3547fa9f6c78e16af85987:f05de262d9b1b3db398d153edf0bf80b)
and the video.mp4 and audio.m4a with the names of the files you downloaded.
Now, if you play one of them they should play normally! This means they're decrypted!! Now the only thing left is to merge them:
ffmpeg -i video_decrypted.mp4 -i audio_decrypted.m4a -vcodec copy -acodec copy final_decrypted.mp4
And we are done! We have converted a video that was playable only in your browser to a normal video file that can be distributed! I hope you learned something from this article. If so, share it with your friends.